FAQ's
Policies
Do you have a formal security policy
Yes. Our policies include a general security policy, technical description of security measures, security incident reporting, root cause, and implementation of corrective measures.
Do you have a Security Incident Response Plan?
Yes.
Roles & Responsibilities
How do customers interact with Mondeca ?
One of the managing partners is always assigned as a customer project sponsor.
Operational contact is assumed by a designated senior consultant (project director during the implementation phase).
Support tickets are recorded, assigned to relevant resources, tracked and escalated to client relationship manager / general management if needed.
Other functions include product managers, functional consultants, DevOps, sales & presales and the general management.
Are background checks required on employees ?
Yes, to the extent permitted by French and European laws. Checks include identity verification, diploma/qualification, previous employment and for foreign citizens, their legal status in our home country.
Are employees required to sign a confidentiality agreement upon hire?
Yes. This is part of the employment contract (in France all employees must have a written contract)
Subcontracting
Does Mondeca send any work functions offshore?
No.
Do subcontractors have access to customer data?
Subcontractors and developers do not have access to client data unless requested and specifically granted by the client.
Do you depend on non-U.S. companies for the delivery of products and services?
Yes. Mondeca is a French company.
Facilities
Where is customer data stored?
Data will be stored in secure AWS data centers. We do not store any client data in MONDECA’s office.
What are the data center security controls?
Please refer to https://aws.amazon.com/compliance/data-center/controls/
How secure is your office space?
Access to the office is controlled. We conduct fire and evacuation drills. We do not have any infrastructure components at the office. Technical and business documents are dematerialized. No customer data is stored in the office. Our office space is a low-risk environment and is not essential for business operations.
Does MONDECA’s office utilize wireless access points for communications?
We use Wi-Fi access points with WPA2-AES encryption.
Architecture
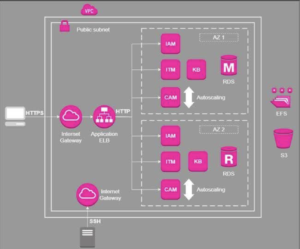
|
VPC |
Isolates the client’s network from external AWS servers and components and the Internet |
|
Firewalls |
Network firewalls built into Amazon VPC. Web application firewall capabilities (create private networks, control access to instances and applications) |
|
Public subnet |
Restricts access from the Internet (Mondeca allows only HTTPS and SSH access through an Internet Gateway. SSH access is restricted to defined source IPs. To increase security, use a VPN for SSH/HTTPS |
|
Security group |
Attached to the VPC (by default, forbid everything and allow only what is described in the security group rules) |
|
SSH Access |
SSH access from a defined source IP is the only allowed external access. All other ports on our EC2s are closed |
|
IAM |
Based on KeyCloak (RedHat SSO) – integrates with Pingfederate, supports Single-Sign-On and Single-Sign Out for browser applications, Synchronization of users from LDAP and Active Directory servers |
Security
What are Mondeca employee clearance and termination procedures?
Clearance includes identity, education, previous employment and alien status (if applicable) verification. The identity verification is performed 3 times: by Mondeca, MONDECA handling our payroll and the French authorities (social security and tax office). Termination procedure includes an exit interview, cancellation of access rights to all our systems, rerouting of professional email (to the extent permitted by French laws), return of equipment and access keys. In case we allow the employee to leave with the laptop, wipe off the storage.
How are clients notified about a security breach?
The client relationship manager notifies the client, evaluates the impact, and agrees on immediate steps. We then issue a detailed report (examples available on request), explain the root cause, describe steps to be taken to avoid it in the future, and seek client approval
How are devices protected from viruses and malware?
Authorized anti-virus and anti-malware solutions will be deployed on all endpoints (including VM), where technically possible. Signature files are automatically updated. Please note that Mondeca is not responsible for the security of customer personnel workstations.
How does Mondeca dispose of obsolete equipment?
Wipe off all data prior to destruction
What are the controls around lost or stolen personal equipment?
Immediate cancellation of the SIM card. Remote wipe if possible. Strong passwords are always enabled.
What are the controls around usage of removable media?
Security policy does not allow the storage of any sensitive information on removable devices.
How is your system protected from unauthorized Internet access?
The application is protected by a firewall implemented with an AWS Security Group. Only Mondeca’s authorized personnel can access the firewall configuration.By default, we set up infrastructures with servers with firewalls with minimal open ports, and with IP filters.
Optionally, a DMZ layer can be added to the infrastructure.
Connection protocols are ssh and https. Intrusion detection is performed with Prometheus to monitor anomalous network accesses. More advanced IPS and HIPS could be set up with AWS cloud infrastructure, for a fee.
How is remote access secured?
Remote access is allowed through MONDECA’s VPN only. VPN access point is in a secure datacenter. Only employees assigned to the project have access. Access rights are reviewed on a monthly basis. Access from non-company assets is not authorized.
Are the connections between the web servers, application servers, and database servers encrypted?
No, unless specifically requested by the customer, internal connections are not encrypted.
All connections happen via SSH. Force brute attacks are limited by strong password policies and failed login attempts limits. They are detected with specific rules set up on the IDS application. SSH access is only allowed within MONDECA’s VPN. All ports and protocols are closed by default, only authorized IPs can access specific ports and protocols.
How is application security tested?
Using tools from the OWASP testing guide recommendations. Tests are executed at build time to ensure that security vulnerabilities are assessed:
- Zed Attack Proxy to detect exposure of sensitive data
- OWASP dependency check for detection of vulnerable dependencies
How do you patch vulnerabilities?
When detected vulnerabilities are fixed and patches are applied accordingly. Specific priority levels and corresponding response times could be included in the contract.
How is client data stored?
Client data is stored in a dedicated database and part of it may be temporarily stored in files on the dedicated server. Client configuration data is stored in files on the dedicated server.
Is client data encrypted?
Data at rest is encrypted in the different storage components of the infrastructure (EBS, S3 bucket, RDS) with encryption using the AES-256 algorithm.
Data in transit (HTTPS) is encrypted by TLS, with RSA certificates by default.
How does the software authenticate to the database?
The software connects to the database via JDBC and leverages native database authentication.
No passwords are hard-coded into the software.
How do you manage sessions?
- Session timeout is 30 minutes by default, and can be configured on the application level.
- Session ids randomly generated by Wildfly’s underlying web server, Undertow, using a Base64 algorithm
- Cookie headers are set with httponly and secure flags
- No data is cached on the browser, except pages of the frontend web application which may be cached by the browser.
How do you manage https security?
Security headers are set to maximum possible security. They are tested using https://securityheaders.com aiming at Grade A.
How is application-level logging organized?
Logs are kept on multiple levels :
- database
- application server
- front http server/load balancer
Provided that it is covered by the contract, logs can be sent to a central log monitoring application from MONDECA’s suite, which includes user-friendly interfaces to explore those logs.
What are your system hardening standards?
Network hardening
- all ports are closed by default
- IP filtering is enabled by default
Server hardening
- users granted right on the base of least privilege policy
Operating system hardening
- OS updates are monitored, and applied
- storages are encrypted
Do workstations store client data?
No. Data is always in secured data centers.
Identity & Access Management
Credentials may be managed in our applications, or by client Identity and Access Management system using the OpenID Connect protocol (on the top of OAuth2).
Are all users uniquely identified?
Yes.
How are users provisioned and de-provisioned?
Accounts are created and removed on IAM by the administrator. We do not provide an automatic user creation process.
How is login information provided to new users?
By sending credentials “out of band” : login by email, password by text message or chat application.
How are credentials protected?
Using AWS Secret Manager.
Are credentials changed from default immediately?
Yes.
What access/identity-related events are logged?
We log the following:
- Account creations, deletions, deactivations
- Account modification dates
- Login attempts
Do you support impersonation?
Yes. The administrator can log in as another person to verify roles, The IAM server allows the administrator to impersonate another user.
How is internet access secured?
Access to all Internet interfaces is protected by an IAM application supporting multi-factor authentication.
Can you use whitelisting for application access?
Connections may be whitelisted by IP address.
Aside from the web-based front-end, are other methods of access supported?
Web services are accessible via HTTPS. Such access is also protected by the IAM application.
How is your API access secured?
User authenticates with Keycloak, then receives a time limited access token.
Can application passwords be customized to client requirements?
The password policy if fully customizable in the IAM application, to enforce different levels of complexity requirements :
- number of digits required to be in the password string
- number of lowercase letters required to be in the password string
- number of uppercase letters required to be in the password string
- number of special characters like ‘?!#%$’ required in the password string.
- number of days for which the password is valid
and many more criteria. Please refer to:
https://www.keycloak.org/docs/6.0/server_admin/#_password-policies
What is your password policy ?
Minimum length of 8 characters and a maximum length of 128 characters Minimum of three of the following mix of character types: uppercase, lowercase, numbers, and ! @ # $ % ^ & * ( ) _ + – = [ ] { } | ‘ symbols.
The policy for password expiration can be configured in the MONDECA IAM server at the initialization of the project, which we set by default at 90 days.
How secure are your stored passwords?
Application passwords are stored and encrypted by the IAM server, hashed using PBKDF2.
Operational Agreements
How are service-level agreements defined?
They are defined in our standard Service Level Policy, included in Mondeca’s Subscription Agreement.
How does Mondeca monitor SLA compliance?
Our deliverable includes a dedicated Monitoring App. The client is able to see the SLA indicators changes over time. SLA’s indicators are reviewed with the client on a periodic basis.
Operations Monitoring
How do you monitor applications and underlying components?
Mondeca’s applications are designed with built-in event logging capability. Information contained in logs is presented in a queryable, user-friendly manner through the MonitoringApp module. Application and Infrastructure events are logged and reported through the MonitoringApp.
How are the alerts communicated?
Through automatic email notifications to relevant staff.
Do you have security tools against malicious activity?
Yes. Antivirus software in laptops and desktops. Modsecurity installed on web servers.
Security tools updates are monitored through the NIST vulnerability feed and the French CERT alert feed.
How are firewall rules reviewed?
Periodically on a monthly basis by a Mondeca sysadmin.
Review includes:
- business justification of rule
- permissiveness
- redundancy
- conformity with security policy (no access to internal networks is permitted)
- usage (removal of unused rules)
- rule author (only authorized personnel may add/change rules)
How do you monitor for intrusions?
Performed internally collecting CloudWatch logs, which are sent to the MonitoringAPP.
How do you monitor for anomalies?
The activity logging process is performed with Prometheus, sending the logs to the MonitoringApp. Alert emails can then be sent when anomalies are detected by the MonitoringApp. Activity logs are periodically reviewed.
What is your approach to application security?
Approach relies on IaaS.
Docker container images are frequently checked for updates at build time (in the CI/CD pipelines). Web application vulnerabilities are tested at build or integration test time with tools recommended by the OWASP report (OWASP Dependency Check, Retire.js, OWASP Zed Attack Proxy, SSLyze)
How do you secure 3rd party software?
Our policy is to use the latest and safest third-party software versions. At the minimum, we use the vendor or community-supported versions.
What do you do with vulnerability scan results?
When detected vulnerabilities are fixed and patches are applied accordingly. Specific priority levels and corresponding response times can be included in the contract.
For published vulnerability patches, we follow the guidelines in the table below
|
Vulnerability severity rating |
Patch installation timeframe |
|
Critical |
8 days |
|
High |
8 days |
|
Medium |
30 days |
How do you act on penetration test results?
Pentests are currently performed by devops, and results generate a report. Actions are taken according to the severity of the risk (immediately vs. in the following days), often to strengthen the rules on the web application firewalls.
Would you allow the client to perform its own penetration tests?
Yes, on condition they target the client platform.
Business Continuity
How can the client continue operations if Mondeca goes out of business?
The customer is the owner of the data and may export them in an software independent format at any time, without having to justify the request.
Who is responsible for security and disaster recovery?
CEO and COO are responsible for issuing security policies, ensuring their applications and reviewing compliance. The CSO role is assumed by the CEO. Mondeca has a dedicated data privacy officer (DPO).
Do you have plans for business continuity?
Yes.
What is the expected timeframe to recover?
Depending on the AWS configuration (single or multi-zone) we agree with the Customer. Less than 24 hours in any case.
How would you notify an outage?
Client relationship manager will notify it’s the Customer contact
Is the capacity of an alternate data center equal to that of a primary facility?
Yes.
Can we run from the alternate data center for an extended period?
Yes.
Do you have an alternate work area?
Yes. Our home office organization is tested and operational.
How often are your continuity plans tested?
Once a year. Tests involve all staff.
Backup & Restore
Our standard policy is to backup separately the entire file system of the client instance and the database containing client data. Backup is encrypted and stored in a different data center.
Backup schedule
Every 24 hours, with a 30 days retention period. May be reviewed for client-specific SLAs.
Backup encryption
Backups are stored on S3 buckets, which are encrypted with the AES-256 algorithm.
Who can authorize the restoration of data?
The client will be asked to confirm that the restore can be performed.
How often is backup and restore tested?
Backup and restore procedures are tested every two months.
How often are backup and restore procedures reviewed?
Every two months.
Data Protection
Do you have a Data Protection Officer?
Yes. Reporting in this role to the CEO.
Do you perform data protection impact analysis?
Yes, for every new customer or internal project.
Do you have processes to detect privacy incidents or breaches?
Yes.
How long do you retain the customer’s data?
For as long as it is required to deliver service to the client. We do not retain information beyond the contract duration, unless explicitly requested by the client.
How do you ensure data is used for intended purposes only?
Access rights are assigned to relevant resources only. In most cases, the client is assigning access rights. Security policy is forbidding downloading information and access to it through applications not intended for operations. Please note that access to client systems is restricted and no data is stored in our office.
Do you use client data for testing purposes?
No, unless explicitly requested or authorized by the client. In most cases, we use generic, publicly available data.
Can we retrieve our data?
Yes. The customer owns its data and may retrieve them at any time in a software independent format, without having to justify the request.
Do you sell or exchange data with third parties?
Never.
Do you transfer EU resident data outside the EU?
No. If you require us to do so, we will rely on the AWS Data Protection Agreement which guarantees the same high level of protection personal data receives in the EEA.
Do you have sub-processor agreements with your service providers?
Yes. Our primary subprocessor is AWS. As all AWS customers we can rely on the terms of the AWS GDPR DPA which applies automatically when AWS services are used to process personal data under the GDPR.
